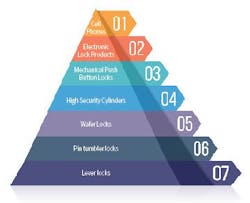
From Keys To Cellphones: A Century of Progress in the Security Industry
Lever Locks: An early lock design was called a lever lock. Lever locks are said to have been invented in England during the late 1700's. A lever lock consists of one or more flat plates (levers), each of which contains a slot. A slot can be located in various positions on the lever. When a correct operating key is inserted and rotated, levers are lifted in unison to the correct heights to form an open slot. A lug is fastened to the bolt mechanism. Continued rotation of the key moves the lug into the open slot at the same time moving the locking bolt to an unlocked position. Modern safe deposit locks continue to use this same lever locking principle. Lever locks generally require long key blanks which are cumbersome to carry in pocket or purse.
Pin Tumbler Locks: As has been written many times before, Linus Yale Sr. and Jr. are generally credited with developing the first modern-day pin tumbler lock system still in use today. Linus Yale Sr. borrowed his first idea for a lock design from that used by Egyptians 4,000 years ago. Yale Jr. later modified the first Yale Sr. lock cylinder design using a small, flat, more easily portable key size. Yale Jr. eventually also designed a combination safe lock system which did not use a key of any kind. Linus Yale Jr. only lived from 1821 to 1868, an amazing amount of useful security products invented in such a short lifespan of only 47 years.
Pin tumbler locks consist of a row of pins which are raised into position as a key is inserted into the lock. Each bottom pin tumbler is held in position by a top pin and spring. When the correct operating key is fully inserted into the lock cylinder, splits between the top and bottom pins are all aligned at a common shearline and the key can be rotated to operate the lock mechanism.
Wafer Locks: A third lock design is the wafer lock. Wafer locks generally use a flat tumbler shape. Each wafer contains a cutout or window and the key is inserted through the windows to operate the lock. Each wafer is driven by an individual spring into a common slot in the housing. Wafers are held partially into the common slot and partially into the lock plug which prevents the lock plug from rotating. Windows are located at different height positions within the wafer. An operating key must have the correct depths of cut to simultaneously lift every wafer out of the housing slot and hold all wafers within the lock plug. The key can then be rotated to operate the lock mechanism. Wafer locks are popularly used for automotive locking systems and for furniture utility locks.
High Security Locks: A fourth pin tumbler lock cylinder design appeared in the late 1960's called high security locks. Pin tumbler locks designed by Linus Yale Jr. required one mechanical action in which bottom tumblers were lifted by the operating key to a designated height called the shearline and the key could then be turned to operate the lock mechanism. Most high security lock designs still contain the pin and top pin feature but also include some type of secondary locking feature.
One of the first high security lock systems was made by Medeco High Security Locks. Specially cut keys were designed to both lift pin tumblers and also rotate tumblers so grooves in the tumblers were all aligned to accept a secondary locking bar. When the tumblers are correctly positioned, the sidebar moves into the tumbler grooves as the key is rotated to operate the lock mechanism.
Several other lock companies quickly introduced their own versions of high security locks containing secondary locking functions. High security locks feature patents on lock designs and key blank shapes. Patents usually are in effect for twenty years. A common practice is for lock companies to develop new mechanical features for their original patented designs in order to extend patent protection. High security locks offer customers key control since patented key blanks are carefully distributed only to registered dealers. Dealers in turn are directed to only furnish duplicate keys to registered customers on record. Secondary locking features also offer added protection against lock picking.
Mechanical Push Button Locks: The first known break from traditional key-operated locks happened in almost the same 1960's time period. An entrepreneur in the lock business named Aaron Fish was asked by the Canadian phone company to product a keyless, mechanical push button lockset. Mr. Fish responded by replacing the lock cylinder in a traditional mortise lockset with a push button unit he called Simplex. Several other domestic and international companies also began offering a full line of keyless, mechanical push button locks in varied forma with installations in commercial, residential, lockers and furniture applications.
Electronic Lock Products: Mechanical locks have always had one major drawback. Anyone with a proper key can operate a mechanical lock and there is no record of the event. Questions as to who and when, often called an audit trail, are not generally possible with mechanical locks. This all changed with the advent of the digital age.
It is difficult to point to one event or product which signaled exactly when the digital age came to the security industry but for our purposes it occurred in approximately 1985. Original introductions of electronic security products often left some need for improvement. Well known companies initially were introducing new electronic products and discontinuing old electronic security products at a dizzying rate as technology improved. Hardwired hardware was usually more dependable than wireless which was often triggered by events outside their intended operational boundaries.
First versions of electronic lock products primarily contained a keypad, were battery-operated and designed for single door applications. Early electronic locks operated similarly to their mechanical counterparts. Electronic components can be easily changed or modified. Additional options such as preventing operation during weekends or holidays, allowing dozens or even hundreds of different user codes, causing a time-out after someone tries too many false combinations, time of usage, recording of use, and quick enrollment of a new user or removal of an existing user increased the versatility of electronic locks and soon moved them from high-end residential usage to mainstream commercial applications.
During the last three decades the basic electronic locking mechanism has remained the same while the means of operating them now has several available options. Keypads equipped with more than one credential increased security. Credentials such as cards and biometrics were added to keypads. With dual credential keypads, sharing a PIN code with someone else was not enough since locks would not operate unless both a PIN and a card or correct fingerprints were also entered at the door. Card technology is continually changing to include smart cards and proximity cards which provide increased levels of security.
Cell phones: At the pinnacle of security today is the use of cell phones to operate electronic locks. Wi-fi allows long distance operation of electronic locks such as remotely opening a door for a family member, acquaintance or maintenance person. Blue tooth technology can be used with a cell phone to send a short range signal to an electronic lock as an owner nears the door entrance. Wireless networks can be used to send and receive signals to operate a series of doors such as in a school environment. The digital age is in its relative infancy. More incredible security products are sure to follow.
About the Author