Five Common Mistakes in Master Keying & How to Fix Them
Simply put, master keying is the art of making one lock operate by two different keys. The difficult part is preventing the lock from operating by using other unauthorized keys.
When an unauthorized key operates a lock, we call that key interchange. There are basically three ways it can happen.
First, there’s manipulation. If the test key is deeper than the correct key, you might get it to turn by wiggling the key. Bump keys are an extreme example of this. Manipulation typically happens when the test key is similar to the correct key or when a lock is badly worn.
Second, there are random outside keys. Each type of lock has only a certain number of possible keys. For example, there are only about 6,000 different KW1 keys. If your front door and my front door have Kwikset 400T3 knobs, there’s about 1 chance in 6,000 that our keys are identical. We generally consider that to be an acceptable risk.
Third, there’s internal key interchange. If I rekey all the locks in a building, and (oops!) key No. 4 operates lock No. 6 when it isn’t supposed to, then that’s entirely my fault.
For all three of these situations, master keying makes it worse.
Whenever we find mistakes, we ask ourselves two sets of questions:
- Where is the mistake? Is the problem real, or does it exist only on paper? Has the system deviated from a good plan, or was the original plan flawed to begin with? This will help us to determine how to address the mistake.
- Does this mistake create internal key interchange or significantly increase the risk of key interchange? This will help us to evaluate the severity of the mistake and decide how to prioritize it.
With this in mind, here are five common mistakes in master-key systems.
1: Documents Not Up To Date
When you take over the maintenance of a master-key system that was created by someone else, you have to see the documentation before you start to make any changes to the system. You wouldn’t expect a surgeon to operate on a patient without first getting their medical history, would you?
The most important documents are the key bitting array (KBA), which summarizes which keys are in the system; the bitting list, which tells what keys are in use; and the keying schedule, which tells which key goes with which door. The bare minimum is the KBA and the bitting list. If you don’t have those two documents, your first task is to acquire them or reverse-engineer them by decoding all the locks and the keys.
Decoding is a tedious and time-consuming task. Often, it takes even more time than what it would take to create a new master-key system and rekey the entire facility. The upside of decoding is we might avoid the inconvenience of tracking down all the key holders and issuing them new keys.
Suppose the client produces a bitting list that has a KBA at the top and a keying schedule. The paper itself is wrinkled and has one or two coffee stains on it. Several ink marks are on the paper, where one item has been crossed out and something else written in its place.
This is actually a good sign. It suggests that someone has updated the documents. Hopefully, the documents would show the date the system was created and the date this version was printed. Ideally, they also would contain a chronological list of “change orders” that detail precisely what locks and keys were changed and when.
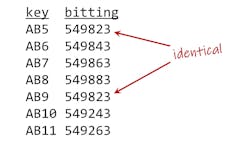
In Figure 1, we have an original bitting list, and we suspect that changes have been made that weren’t recorded here. The previous locksmith isn’t available to answer our questions.
How serious is this problem? Failure to update the bitting list certainly can lead to key interchange. In fact, it might have happened already, and we just don’t know it yet. Our task is to find out how much of it remains accurate and how much has changed. Where do we begin?
Let’s speak with a few key holders, ask them whether they remember when a lock was rekeyed or a new key was issued. That could give us an idea of how much has changed over the years. In this example, the final key on the original bitting list is labeled 22AA, and the most recent new key that we know of is 25AA. This suggests that the system has been changed three times (maybe more). Identifying those three changes would be a good place to start.
Progressing from the KBA will tell us all the keys that were intended to be used in this system. Assuming that the previous locksmith followed this plan, we know what keys 23AA, 24AA and 26AA probably would be. We have key 25AA in our hands, along with a copy of the AA master key. We can walk around the facility, trying these five keys in every door. Hopefully, 26AA won’t operate any of the locks, which would mean it’s the next available unused key. Then we’ll update the bitting list and the keying schedule.
This might take several hours — or even several days. But what if the client can’t wait that long? Suppose they have to have door 307 rekeyed right away, at 4 p.m. Friday.
What can we do? We might be tempted to rekey door 307 to 26AA, the next key in the progression. But that would be like a surgeon operating on a patient based solely on medical records from 20 years ago. Can we be confident that 26AA hasn’t been used already? If we use it again, we could create key interchange. Fortunately, there’s another option.
We can rekey door 307 temporarily to a random single key, with no master pins in the lock. We still have a tiny risk of key interchange, but it’s no worse than the risk we accept from random outside keys in any single-keyed lock. This will get us through the weekend, and then we can continue on Monday with our task of updating the documents. Then, we can assign an unused change key to door 307 and master-key it under the AA master.
2: Damaged Locks, Bad Keys
This is a rather broad category, including worn keys, keys that were cut slightly too deep or too shallow and locks that have filed plugs, empty chambers or incorrect driver pins. Why would these problems persist? Why didn’t the previous locksmiths take care of it?
What they should have done is recut the keys. When you find a filed plug, check to see whether the keys are cut accurately. If not, make fresh originals on a code machine and check them with a micrometer. Then, toss away the cylinder that has the filed plug and replace it with a new one.
Unfortunately, this might not be the end of the problem. We don’t know how many copies of those poorly cut keys are floating around. We might get numerous complaints from key holders who say their old keys don’t work anymore or work only intermittently. We seriously should consider rekeying that lock to a different change key, which would force each key holder to discard their old key and get a new one.
Empty pin chambers typically are a mistake but not always. In certain low-security applications, leaving chambers empty can make the lock more reliable, particularly if the alternative is stacked master pins.
Consider the case of a restroom in a lobby. It could have a privacy lock on the door, but someone decided that it would be better if guests asked the receptionist for a key to use the restroom. What’s the downside of leaving chambers empty here? Technically, we’d create key interchange, but does it matter in this case? We aren’t trying to keep someone from picking the lock to steal toilet paper. We just want something slightly better than a privacy lock. Empty chambers might be appropriate there.
3: Progression Errors
Figure 3 has an example where the same bitting appears in the bitting list twice. Unfortunately, mistakes of this type might go undiscovered for a long time. Users generally report it right away if their keys won’t get them in where they have to go. But if a key lets them in where they aren’t supposed to be, they have less of an incentive to report the problem. In fact, they might not even be aware that it’s a problem. They might just assume that their key was intended to operate that lock for some unknown reason. They might shrug it off.
Take a copy of the offending key to both doors and try it. If the key operates in both places, the problem is real. The way to fix it is to rekey both locks and assign each of them to a new key.
You might be tempted to rekey just one of the locks and retrieve all the erroneous copies of the key. The problem with that is you can’t be sure you received all copies. There might be more copies you don’t know about. This is particularly true with unrestricted keys that could be copied easily at a local hardware store.
In our example, we found that AB5 and AB9 are identical because of a typo. The AB9 key should have been 549223. This mistake creates internal key interchange. We have to find, in the keying schedule, all the locks that use either the AB5 or AB9 key.
All those locks must be rekeyed. If AB11 is the last key in use under the AB master, the two new keys will be AB12 and AB13.
4: Master Key as Change Key
This problem is a little worse than a repeated key and a little more difficult to spot. Suppose you get a report that the AD5 key operates a lock that’s supposed to be operated by AD3. You check the bitting list and see that AD3 and AD5 aren’t identical. The next step is to see whether AD3 and AD5 have the same number of constants.
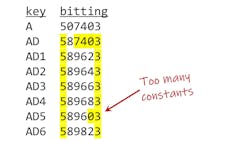
If we look closely at the example in Figure 4a and count the constants in each change key, we see that most of them have only two constants, but the AD5 key has three. This is a mistake. It means the AD5 key is more similar to the A grandmaster key, which means the AD5 key is more powerful than the other AD change keys. It has one extra constant — the zero in the fifth chamber. A key that has one extra constant is called a one-pin master, which typically means it will operate four different locks. Common examples of one-pin masters are block masters and row masters.
How did this happen? This isn’t immediately obvious in list format. It’s easier to see in standard progression format. Figure 4b shows the same bitting list as in 4a in standard progression format. 589603 is a block master, so it shouldn’t be used as a change key. We should check the entire system to see whether this mistake might have been made more than once.
In this example, the AD5 key will operate locks AD1, AD2, AD3 and AD4. Once again, we might be tempted to just rekey the AD5 lock and retrieve all the AD5 keys, but that doesn’t really solve the problem. We have to rekey locks AD1 through AD4. In fact, the AD5 lock is the only one that doesn’t have to be rekeyed. We could leave the AD5 lock as it is if we wanted.
There are some rare circumstances where it’s OK for some change keys to have fewer constants than others, but 99 times out of 100, it’s a mistake. In the extreme, you might find a system where the number of constants appears to fluctuate randomly. This brings us to the final mistake on my list.
5: Shoebox Master Keying
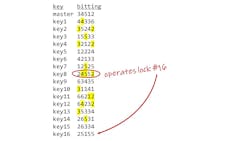
In this situation, the plan itself was flawed from the beginning. Professional master keying requires a logical plan and careful record keeping. It might be tempting to just pick change keys randomly, such as grabbing them from a cardboard box. Shoebox master keying relies on luck to avoid key interchange. And luck will run out sooner than you think.
What can we do to fix this? Most important, we have to rekey lock No. 16 right away. But that doesn’t fix the underlying problem, which is that the keys don’t all have the same number of constants. For the long term, we have to decide how many constants this system should have and rekey any locks that don’t fit that plan. We also must identify which keys should be avoided in the future. This can be complicated. In many cases, it’s much easier to just start over with a new master-key system.
What if the customer doesn’t have the funds in their budget? Here’s a suggestion: Create a new master-key system — but not all at once. Switch over to the new system gradually. Let’s call the old system “A” and the new system “B.” Make sure the B system is designed properly and well-documented. Mistakes that existed in the A system eventually will become irrelevant. You could take a week, a month or a year to make the switch. During the transition, your customer just would have to carry two master keys, A and B. It’s a minor inconvenience.
That’s my list. If you keep an eye out for these five common master-keying mistakes, you’ll be better prepared to fix them before they get out of hand.
Ralph Forrest-Ball, CML, is a locksmith, instructor and the author of “Mastering the Basics of Master Keying.”
About the Author
Ralph Forrest-Ball, CML
Ralph Forrest-Ball, CML, is a locksmith, instructor and the author of “Mastering the Basics of Master Keying.”