The Skinny:
- Both residential and commercial markets are shifting from traditional hardware to cloud-connected, app-driven systems, prioritizing software functionality, convenience, and lower costs.
- Consumer expectations are rising, especially among mid-tier homeowners and small businesses.
- While mobile credentials are gaining traction for access control, widespread adoption is still limited by technical complexity and legacy preferences.
Advances in security technology are disrupting both the residential and commercial markets, as homeowners and business owners transition from traditional hardwired security systems and off-line locks to cloud-based connected systems, smart locks and products that can be controlled and monitored remotely using your phone. This culture change reflects an overall shift in focus to the software that is controlling the hardware, including all these new smart connected devices and systems.
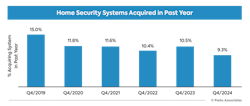
Currently, less than 10% of security system owners (see graph) report purchasing their system in 2024, a nine-year low, according to the latest research from Parks Associates in partnership with Ubiety Technologies.
“With more choice than ever in security solutions, consumers expect smarter, more efficient, and less expensive solutions,” says Jennifer Kent, vice president, Research, Parks Associates. “The need for lower costs and more efficient security solutions is triggering a reevaluation of where the most value lies in security systems, particularly as software-based solutions enhance scalability and reduce costs for both providers and customers.”
Who’s Driving Decisions?
As Chad Lingafelt, managing partner, Loc-Doc Security, points out, much of the buying decisions on the residential side tie directly back to home values, noting three major categories of home pricing: sub $500,000; $500,000 to $1.5 million; and $1.5 million and up.
“If you just look at it in those three categories, the $500,000 and below are typically going to be a DIY consumer, especially when it Is relative to locks because they can get it at Home Depot or Lowe's or Amazon — there are value priced options out there,” Lingafelt explains. “So, they're going to be able to get a lot of value-priced hardware, and from a consumer standpoint, the manufacturers have made those products so easy to install. They've simplified the programming; it's all very app driven, so it is a good DIY product.”
When you get into the $500,000 to $1.5 million homes, they are going to be more likely to sub-contract out installations. “They're going to typically be more price aware and they're going to be focused on ease of use, and the convenience side,” he says. “And those are typically folks that are looking for a connected and very integrated solution that's going to tie into their alarm system, and that's app driven, so they're focused on a monthly fee versus a one-time purchase.”
When you get into $1.5 million and up homes, Lingafelt says those are typically customers who are exclusively contracting everything out, especially when it comes to security around the doors – the locks, the cameras, “anything security related, really,” he says. “They're typically using a contractor to make all those decisions and they’re not the ones that are looking for those products.”
He continues, “So, the biggest influencer around all that product decision making really comes down to the person who is living in the $500,000 to $1.5 million home because he's the contractor for the guy in the $1.5 million and up home and he's making decisions that are based off of his experience.”
Lingafelt is seeing this same kind of distinction when it comes to small businesses compared with larger corporations.
“If I'm running a small business that's doing, say $750,000 a year in revenue, I also have limited resources because I am probably netting 10- to 15%, for example, so I'm cost conscious,” he notes. “I'm not going to go pay a commercial security company to come in and put $1,000 locks on the doors. I'm going to buy the $150 lock that I can install myself because I did it at my house. And I'm probably going to get cameras myself because I can set it up and do it all from my phone.”
But as Lingafelt points, the larger corporations are the ones who will start to pay for professional services and installation and management from a security professional.
Raising Expectations
The demand for more sophisticated systems and lower price points continues to create challenges for locksmiths and other security providers, as well as raising expectations for their customers.
“The value of security devices and systems is in the benefit they provide – the use case unlocked, rather than the hardware itself,” says Kent. “Functions that can be virtualized into software — like knowing that someone is home, knowing who that someone is — or combined into multi-functional hubs (e.g., detecting environmental inputs like light, temperature, humidity), are most likely to shed their hardware casing.”
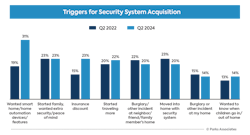
Software-based security solutions enhance scalability, efficacy, adaptivity, and flexibility while reducing costs for both providers and customers, with 38% of security system owners who purchased their system in the past two years citing demand for smart home features that enable situational awareness and convenience as a purchase trigger, compared to just 22% of those whose systems are five years old or older, Parks finds.
“Providers who embrace software-defined value, invest in differentiated professional monitoring, and meet consumers where they are — at the intersection of convenience, cost-effectiveness, and intelligence — will lead the next era of secure, connected living,” says Kent. “Providers must be able to deliver a security experience that attracts and retains customers at a cost that is competitive, while also yielding competitive margins.”
Battle of the Credential Continued
As access control technology advances, 61% of security leaders say that mobile identity proliferation — or the shift from traditional physical credentials to mobile-based identities — is among the top three trends, according to data from the 2025 HID State of Security identity report, with almost two-thirds of security leaders having either deployed (37%) or planning to deploy (32%) mobile credentials for access control.
“We have seen an increased adoption of mobile credentials since we started the survey,” says Matt Winn, VP, Communications for HID. “We see it's continuing to grow in adoption and in use cases. So, yes you can leverage it for access control, but there are also a lot of different purposes you can use it for, whether it's Apple Wallet or Google Wallet. You can use it for secure time and attendance, your parking garage, so many examples.”
Built-in safeguards also make mobile credentials safer for organizations, driving continued adoption, according to the report, noting that features such as biometric authentication and encrypted communication provide robust protection against unauthorized access, while remote management allows for quick updates or revocation of credentials.
The HID report highlights some additional drivers for continued adoption:
· Mobile credentials Integrate seamlessly with smart building technologies, supporting scalability.
· They align with sustainability goals by minimizing waste. Sustainability efforts are realized with mobile credentials because of the reduction in physical card production (eliminating plastic waste from traditional cards), replacement and maintenance, and align with the growing demand for eco-friendly solutions.
· Mobile credentials also deliver valuable insights through real-time access tracking and analytics, aiding security audits and operational planning.
Challenges to Mobile Adoption
While mobile credentials eliminate the need for physical cards or fobs and allow for a streamlined experience across multiple use cases, presently the broad majority of security
leaders (84%) are still using a mix of mobile and physical credentials, citing the need for different credential types for different user groups, such as employees and visitors, according to the HID report.
While mobile access may be a good fit for some, like higher education, there is still a need within many verticals for that physical identification, usually in the form of a badge, with 48% of respondents noting that visible identification is still a requirement within their facilities.
“When we asked [survey respondents] if they continue to use cards, the majority of them said yes and that they plan to continue to do so,” says Winn. “And the number one reason for that was because they needed a visual identifier, especially in a vertical like healthcare or government, or you think of an airport staff worker. So, while we are seeing a proliferation and adoption of new use cases for mobile, the card still remains important our findings show.”
While technology continues to provide more convenience when it comes to access control, the evolution from cards and fobs to mobile credentials is one that will take time, especially within the commercial sector, adds Lingafelt.
“I would like to see more of the acceptance of mobile credentials,” he says. “I'm a firm believer that [lifts phone] this is my credential for everything in my life, but I don't think that the deployment of it is as easy as the manufacturers think that it is, and so [security professionals] are not selling it at the same rate that we would like to see it implemented.”
Lingafelt notes that many businesses are not to the point where they are willing to invest the time and resources to realize the full potential for mobile credentials, as “it's much more achievable on the residential side,” he says. “For example, you can go buy a lock off the shelf today, connect it up to your Apple home kit and you're up and running. It's not the same way on the commercial side, as the adoption of it there is significantly more complicated, especially when it comes to Apple Wallet integrations. There are a lot of hurdles to jump through. So, what is the path of least resistance? Right now, the path of least resistance is an electric strike, a card reader and a FOB. It's the known, it's easy and It's what everybody's been doing.”
Overall, as Lingafelt points out consumer demand is still not driving widespread adoption right now because there are not enough successful applications where it is making it necessary for others to change what they are already doing.
“If you look back, Apple and Google originally launched their wallet application in 2015, so wallet has been out for 10 years, and many retailers are just now offering it,” he says. “The more that that adoption pushes it to where it makes it easier for people to use that technology, the more ubiquitous it will become.”
We are getting to the point where our phone is becoming the credential of choice across many form factors, whether it is for identity, unlocking doors, paying for things, etc.
“We’re getting to where the only credential that I'm carrying is also a physical key to my house, or for my business,” says Lingafelt. “And when we get to that point, then consumers are going to be saying, ‘Hold on a second, I can drive down the road and use this as my driver's license, as my insurance card, to pay at restaurants and retailers, but I have to carry this obnoxious credential around?’ That's when it's going to start driving the impact. We're just now seeing a real functional adoption to mobile credentials for just consumers.”
About the Author
Paul Ragusa
Senior Editor
Paul Ragusa is senior editor for Locksmith Ledger. He has worked as an editor in the security industry for nearly 10 years. He can be reached at [email protected].