How To Protect the Security System from Hack Attacks
It is entirely possible that the control and convenience of Electronic Access Control (EAC) can render a door less secure than a good mechanical keyed lock. Every reader of this article will be aware that there are elements that vary widely in their physical security attributes. An EAC can be implemented well or poorly, potentially causing security vulnerabilities.
This article focuses on protection from Hack Attacks. It does not address the access control concepts of forced and held alarms, nor the interaction with a potential burglar alarm. While these are often useful attributes, they are outside the scope of this article. Here are four cyber security areas for consideration:
- Basic network security concepts
- Data to panel communication
- The card and reader combination
- The underlying security system architecture
Basic Network Security Concepts
It used to be that a person had to be on-site to get in, cause damage, or steal something from a site. But with the connectivity to the Internet, virtual access renders all connected systems vulnerable. There is no way to know where or what all the vulnerabilities are. The systems are too complicated. Industries have developed to try to manage and control various aspects of cyber security. Every day, new vulnerabilities are created with the addition of new “opportunities and functionality.” And every day, new vulnerabilities are found by hackers, and spread through the hacker community over systems like the Dark Web. It is important for security suppliers to be cognizant of the general rules and basic opportunities that are available to secure the security systems.
Where the router software allows it to be used as a firewall, close the security system port to all types of traffic and all internet addresses with the exception of the ones that are required to make the system function. For small systems, the customer’s router is likely to be supplied by the Internet Service Provider (ISP) and will often have both WiFi support and multiple inside RJ45 ports, along with 5 outside facing IP addresses. End users, potentially with the help of a security installer, have the authorization and the responsibility to set up the router to be secure using the web browser for the router. This means that it would be possible and wise to assign one IP address to the security system while leaving all other customer traffic on the a primary IP address. A technology called Network Address Translations (NAT) allows the actual address of the internal device to be set to a non-routable IP address – one that can’t be sent over the Internet. This separate port should be set to NAT the public IP address from the ISP to each internal un-routable device IP such as a panel. This will isolate the traffic for the security system from all other client traffic. This is valuable in two important ways:
First, if the security system is compromised, it would serve little purpose for the hackers to weaponize the security device to attack the Customer since the security is in its own isolated environment. This will lower the potential liability if anyone were to hack this device.
Second, if the Customer’s network is compromised, the hacker will have no access to the security system.
For every network device, the default passwords should be replaced with a high security password that is difficult to hack. These passwords can be kept in a secure place and at a backup location, since they should generally not be something that is attempted to be remembered. Set different passwords for different devices. If multiple people use the system on a regular basis, they should each have their own password to each device that they use. In most cases, they will only be connecting to one device. If a person is accessing a device often, then a pass phrase will be better than a single password.
- Eight characters is the minimum password length, but make them at least 10. Each added character adds approximately a power of 70 to the combination. Greater length is better than greater complexity against brute force hack attacks.
- Make sure that there is no meaning to the password, no dictionary words, and no numbers that are letter substitutes for actual dictionary words like the use of 3 in place of E.
- Use upper case, lower case, numbers, and special characters.
- Don’t use repeated numbers or characters.
Where there is a server and database for which the installer is responsible, it is imperative that the operating system, database, application, and any other software be kept current and patched to remove known vulnerabilities.
Data-to-Panel Communication
The most common electrical protocol used today between card readers and panels is called Wiegand Protocol. This protocol is unidirectional with data flowing between the reader to the panel, but not the other way. Multiple approaches as to how to accomplish a Wiegand hack are on the internet.
A newer, and not as widely available, protocol is Open Supervised Device Protocol (OSDP). OSDP is commonly available from card reader manufactures, but only available from some of the panel manufacturers. OSDP V2 with secure channel supports 128 bit AES encryption. It would be wise to utilize OSDP where reasonably possible instead of Wiegand.
Cards and Readers
Card technology has changed significantly from the very early days of access controlled doors with magnetic dots or holes in the card. These were extremely easy to decode. The next big thing was a magnetic stripe, similar to that which still exists on most credit and debit cards. Early proximity cards were inductive – capacitive loops. Proximity (Prox) cards became the next standard. Prox cards are electrically energized by a 125kHz field from the reader. Once powered, they spit out their card number.
Subsequently, various technologies started using a higher frequency, 13.56 MHz, allowing for more information transfer in a shorter time. Since quick reads were, and still are, important to the feel of the end user, this allowed for technologies like Mifare Classic by NXP and iClass Classic by HID to provide a simple encryption key for the cards and readers. These encryption keys are symmetric, meaning that the same key is in every card and key for a particular system. Since most systems serve very few doors, these symmetric keys are common across most systems, with the opportunity to make them unique.
The above technologies fell to the hackers and were compromised. So today new technologies are available with better keys and challenge-response processes that take place between the cards and readers. Three examples of currently un-hacked technologies that are widely available are NXP’s Desfire EV2, HID’s SEOS, and Oberthur’s OTSmart. These are all symmetric keys, but have challenge-response controls that the industry considers secure when implementing them in today’s 2018 world.
A last note on card technology is important for perspective. The U.S. government has dictated that all government agencies and all government contractors utilize an asymmetric keying approach in their access control systems. These cards utilize a public-key, private-key system called PKI that makes each key unique. The infrastructure for this card approach is extensive and is not economically viable for the general commercial market today.
Underlying System Architecture
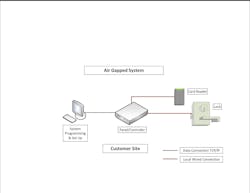
Figure 1 shows an Air Gapped system that is local to a site. This system is not vulnerable to an Internet hack because it is not connected to the internet. This may be a perfectly good approach for a small site. However, if installers need to look at, check the system, or fix some of the set up programming, they will need to make a site visit and most likely connect to the system with a laptop using a web browser. This architecture approach is called “air-gapped” because there is no connection to any network. Depending on the on-site architecture of the system, local on-site vulnerabilities may be created which can usually be addressed by physical protections like physically locking the EAC panel. This system will operate with the laptop disconnected.
If the concept of the installer being able to service the customer over the Internet is useful under the context of either support or database management, such as adding new user card and controlling the access restrictions of “who can go where,” then there will need to be an Internet connection. Figure 2 shows a Hosted System where the installer hosts a server and database and the customer site has one or more panels. The installer can access the server locally and can keep the system current. These panels respond to a card presentation at a reader. If the card is in the panel’s database and is authorized for the door that has that reader, then the panel will let the person in by unlocking the door. This transaction will then be sent to the server.
It is important to know that the panel is all that is required to let the person in. If the internet connection to the server is down, the person will still get access. When the Internet comes back up, the stored history in the panel will be sent to the server, making the audit record whole. In this design, the networking security controls are programmed into the Customer’s router and into the panel.
While Figure 2 shows the server with its database at the installer’s site, it could alternatively be located at the customer’s site. With this architecture, the customer’s router would be connected to the server with its database and the cyber security controls would be primarily in the client router and the server. The connection between the server and the panel would be local and less likely to be attacked.
Figure 3 represents a Cloud System EAC where many of the security concerns are managed by the EAC supplier. At either the Installer’s or Customer’s site, the system can be configured, managed, and controlled using a web browser. with encrypted communication. All the security updates for the operating systems and databases are kept current by the supplier. At the client site, the panel(s) would be connected to the router. If there are multiple panels, then a switch could be used to allow the multiple panels to each have access to the Internet.
The recurring revenue model of a cloud EAC is a good long-term business strategy. The cloud supplier covers the cost of keeping a server, database, and web portal secure. The system would be on a high availability infrastructure. Therefore, the cost to the installer is minimized and isolated to getting the system installed and doing any system management for the client. All the router recommendations would still apply.
Where the number of doors becomes larger than one panel or controller, it is possible to add more door controllers. These may be IP or asynchronously connected. With asynchronous wiring, like RS485, there is no cyber vulnerability. An example would be a controller connected with RS485 communication to a set of door boards that are used to connect more readers and locks.
If the door connection devices are IP based, then it would be useful to use a switch that is isolated from the Client’s network, maintaining the isolation at the router level. With the right level of sophistication of the network programmer, it is possible to use a virtual LAN (VLAN) and put the IP devices on the client’s physical LAN. However, this is a potential source of complexity, confusion, and system problems that are probably not worth the savings of not using a separate switch.
Harden each Ethernet connected device by never using default passwords, turning off or preferably removing all unused features, and turning off all unused communication ports. Depending on the nature of the IP field device, there may be a number of things that need to be shut down and/or removed. It is advisable to set port security for each utilized switch port to “shutdown”, which will help to secure the SLAN at the field locations. This has a penalty of more activity, if there is a device disconnect or problem, as it will require connecting to the switch to reset the port. The shutdown will make it more difficult for someone to physically inject a device at the field end into an SLAN.
8 Basic Cyber Rules:
- Isolate and “air-gap” where reasonable
- Limit communication opportunities to just what is needed to operate
- Limit IP access to field points by using Asynchronous communication or an SLAN
- Put central components in a secure environment
- Replace all default passwords with high security passwords
- Harden all field points
- Put controls and constraints on each Internet connection
- Document each setting in each device
Ed Chandler, CPP and Lorna Chandler, CPP are principals at Security By Design, Inc. located in Pacheco, CA