By using Generics, locksmiths can easily develop master keys, or develop key characteristics from key bittings.
Generics can simplify how we consider and work with incidental master keys.
The last article (October 2004 Locksmith Ledger) demonstrated how to determine the power and characteristics of a random key in the master key system by decoding the key bittings. Generic Types were used to target how the key performed within the master key system and on a page, demonstrating the power of the key.
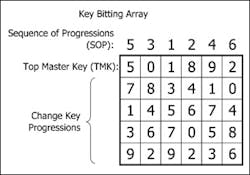
This article will demonstrate the reverse. A Generic Type will be selected from within a master key system, and the key bitting will be determined. To do this, you will need the Key Bitting Array (KBA, Figure 1) and a worksheet specifically designed to determine key bittings from Generic Types.
Before starting, let' s review what a Generic Type is.
In Figure 2, the KEEWERX template, the mechanism that creates Generics is px. This refers to the relationship to the number of change key bittings under the master bitting. In the KBA, this is expressed as rows for change key bittings and columns for the number of key bittings.
With most systems, there are four change key bittings under the system bitting in the KBA. When "p" in px equals 4 (the rows) and "x" equals the 6 (the columns), the results are 41+1+1+1+1+1 or 46 or 4x4x4x4x4x4, or 4096. This is the total amount of change keys that can be progressed in a standard six-pin master key system.
Other systems have five, six or seven change bittings under the master bitting, so the "p" in px accommodates all of these master key systems. As a system progresses, Generics are created. The term px can be used to express how the master key system progresses.
At p0, the beginning of progression is occurring in the first column. At p1, the first column is fully progressed and current progression is ready to start in the second column. At p2, the first two columns have fully progressed and current progression is starting in the third column. At p3, the first three columns have fully progressed and current progression is starting in the fourth column. At p4, the first four columns have fully progressed and current progression is starting in the fifth column. At p,5 the first five columns have fully progressed and current progression is starting in the sixth column. At p6, all six columns have been fully progressed.
Table 1 (page 36) reveals the creation of a Generic during steps of standard progression. There are only eight Generics Types: X0; X1;X2;X3; Y1; Y2; Z1; Z2.
For every three columns that progress, a new level of keys are created. The first three progressed columns create a complete hierarchy of key functions for each page of the master key system. The next three progressed columns create a hierarchy of key functions that occur within the pages of the first hierarchy.
This article is limited to Generic activity within 5- and 6-pin systems. Note that this process continues infinitely and that is there is a P7 (when dealing with 7-pin systems, etc).
Generic References for 5- and 6-pin systems are visually designed to reveal where and how the key functions. To do this, the Generic Reference is separated into two parts, a prefix and a suffix. We will examine the Generic Reference and its two components.
Consider the Generic Reference for a change key: X0X0. The first two characters represent the first Generic Type XO (the prefix), and the remaining two characters represent the second Generic Type XO (the suffix). Generic Types in the prefix position represent how the key functions throughout all pages. Generic Types in the suffix position represent how the key functions on a given page.
The numbers in both designate the power of the key. In the case of X0X0, the key operates keys on a single page, and can only operate a single change on a page (See Figure 2).
As a second example, consider the reference: X0X3. This key operates keys on a single page (p0=40), and can operate 64 (p3=43) keys on a page. Remember the numbers always reveal the power of the key (p3).
Find the Key Bittings
from a Generic Type
To maintain consistency, the Key Bitting Array (KBA) and the Generic example used in the last article will be discussed: Y2X2. Refer to Figure 3 as the worksheet titled: "Develop a Master Key (6-pin)."
The Key Bitting Array was filled out using the provided KBA in Figure 1.
As shown in "Step 1," the selected Generic (Y2X2) was split into two equal parts and entered on the "A" and "B" line.
In "Step 2", any cuts in common with the TMK were identified by following the instructions: The part of the Generic that was entered on the "A" line, "Y2" is located to the left (row header) of the Alignment Chart. Any 6, 5, or 4 that appears on the same line in the Alignment Chart is circled. In this case a "6" and "4" was circled.
The part of the Generic that was entered on the "B" line, "X2," is located to the left (row header) of the Alignment Chart and any 3, 2, or 1 that appears on the same line in the Alignment Chart is also circled. In this case a "2" and a "1" was circled.
In "Step 3" the Sequence Of Progression (SOP) from the KBA is transferred down into cells provided to the right of the step. The number in each cell is compared to numbers circled in the Alignment Chart. If a circled number in the Alignment Chart matches the number in the cell, the number in the cell is also circled.
In "Step 4", check each cell in the "Step 3" to see if it is circled. If it is circled enter the number from the TMK line in the KBA that appears in line with the same column. Do this for each cell. In the example the first two cells in "Step 3" were not circled, so nothing was entered into the cells in "Step 4". The last four cells in "Step 3" were circled so the numbers that appear on the TMK line of the KBA were entered into each cell of "Step 4."
Any change key is entered into the cells of "Step 5." This is usually a change key that is being used for a specific master key project in which a master key is needed.
The final step, "Step 6," integrates both the selected change key ("Step 5") and the cells that were entered in "Step 4." For each cell to the right of "Step 6," enter the same number, in the same position, from "Step 4". If the cell is blank, enter instead, the number from the cell in the same position from "Step 5".
When completed, the key bitting for the master key, Y2X2, appears on "Step 6."
A blank worksheet (Figure 4) is provided so that you can use this procedure to determine master keys for your own master key systems. Although the worksheet seems to work like a magician's number trick, it simply relies on the tried-and-true premises already established in Standard Progression Format (SPF). Each step in the worksheet is designed to "guide" the locksmith through a process that enforces SPF rules.
A crucial step in the worksheet is guiding the locksmith through the implementation of the Alignment Chart. The chart is deceivingly simple, even though much research has gone into its creation. The Alignment Chart is a table that notes when and where TMK bittings will appear in a targeted key. It charts the evolution of master keys as keys sequentially progress. The Alignment Chart in Figure 3 is designed for both 5- and 6-pin systems.
Developing a Key Bitting Array when it doesn't exist
Essential to good master keying procedure is the establishment of a static Key Bitting Array.
Locksmiths tell me many of their existing master key systems do not come with a KBA, rather they exist in the form of pages of records. Lock manufacturers often provide these pages to locksmiths, not as a complete "book" but as the part of the "book" that the locksmith currently needs. For these locksmiths, there is a process to determine the original Key Bitting Array.
When information is not readily available to complete the KBA, a decision has to be made. If support regarding the existing system is ongoing, you will need to discuss the completion of the KBA with the source of the existing system.
If no updates are anticipated, the KBA can be carefully filled-in by honoring the rules of Standard Progression Format.
Here are the rules to follow:
Regarding the sequence of progression, each number represents the order in which the columns progress; therefore, numbers have to be sequential and cannot be repeated in the SOP.
When filling in missing change progressions, remember that TMK bittings (in the same column position) must not appear in the change progression cells. This would cause unwanted interchanges of change keys.
Each column of change progression cells must use unique numbers that are part of a working subset for the column. For example, in any given column a working subset might be {1,3,5,7,9}. If the TMK bitting is 5, then the remaining available numbers are the subset {1,3,5,9}. In a column of change progression cells, these four numbers would be entered in the cells in any order.
Once the KBA has been established, all worksheets described in this article can be implemented.
Table 1. Creation of a Generic